Impending Multi-Factor Authentication system addresses cyber protection in Grand Valley State University students’ accounts.
Many students have had their GVSU accounts, emails and login credentials compromised in recent years. Such instances have incentivized GVSU to make a Multi-Factor Authentication (MFA) system mandatory, requiring students to verify themselves with each login starting May 6.
MFA has always been an option for GVSU students when setting up their accounts. However, frequent cyber-attacks on campus have pushed the University to make MFA a requirement for students. As the policy rolls out, students can expect to spend more time logging into their university accounts and applications beginning next month.
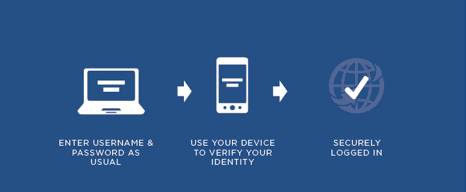
MFA works by requiring each student and university employee to verify each login through Duo, a secure authentication service that helps protect sensitive information and prevent unauthorized access to university systems and resources.
When attempting to log in to any GVSU application, the user will be prompted with code on their attempted login device. To gain access, users will have to enter the code into the Duo application on their cellphone. Duo will open a prompt on the user’s phone, making the process as simple as possible. To help visualize this process, a demo can be found on the Duo website.
The authentication process will be required for login to all GVSU applications, such as Blackboard, Handshake and Banner. By linking all apps, logins and devices into a unified account through Okta, an access management company, users can streamline their access to university resources– all secured through Duo.
The enrollment process may come with some inconvenience or confusion, like extending the time it takes to access applications like Blackboard and Workday. This authentication process has already been introduced for GVSU faculty.
“I know the MFA can be a pain,” said Anthony Spencer, Professor and Graduate Program Director for the School of Communications. “However, I think it is worth the inconvenience to keep our data safe.”
Protecting information and data privacy is a priority for GVSU. This challenge is particularly evident among universities, many of which have experienced a torrent of cyber-attacks and information theft.
The Federal Bureau of Investigation (FBI) published notices to inform colleges across the United States that several university credentials were compromised, further pushing urgency in profile encryption and data protection at academic institutions.
“(The) FBI has observed incidents of stolen higher education credential information posted on publicly accessible online forums or listed for sale on criminal marketplaces,” according to an FBI disclaimer.
Duke University has been victim of multiple phishing attacks. In 2022, attackers used a two-phase infiltration tactic, first using non-Duke email addresses to urge students to disclose sign-in details to prevent losing access to their accounts. Subsequently, attackers utilized the stolen passwords to initiate another round of attacks, this time from Duke email addresses, with the aim of acquiring financial data.
Grand Valley Police Department (GVPD) is familiar with phishing scams and cyber-attacks on campus.
“We often see fake virus protection, telling students that their device has a virus and prompting them to use a malicious link which actually contains a (real) virus,” said GVPD Captain Leah Heaton.
Exposing usernames and passwords can lead internet hackers and online scammers to use a technique called credential stuffing to make the most of leaked logins. Credential stuffing is a type of cyberattack where attackers use stolen usernames and passwords from one source to gain unauthorized access to user accounts on another platform.
Such attacks pose a danger especially to those who use the same passwords and usernames across various websites. This can threaten credit card information, lead to fraudulent transactions or initiate subsequent attacks on affiliated websites and organizations.